Challenge & Solution

Problems
- Unauthorized devices accessing internal networks
- Delayed or manual enforcement of policies
- Sensitive data transmission without encryption
- No way to track/report device misuse or loss
Solutions
- Auto-enforce security profiles by department
- Secure encrypted messaging and file sharing
- Monitor device health and usage remotely
- Lock or wipe lost/stolen devices immediately

Secure Tablet & Mobile Device Management
Strengthens endpoint security across government-issued devices through centralized policy enforcement and remote administration.
Products

Enforced Security Policies & Data Leakage Prevention
Enforces strict compliance to protect sensitive government data, preventing leaks through real-time monitoring and access controls.
Products
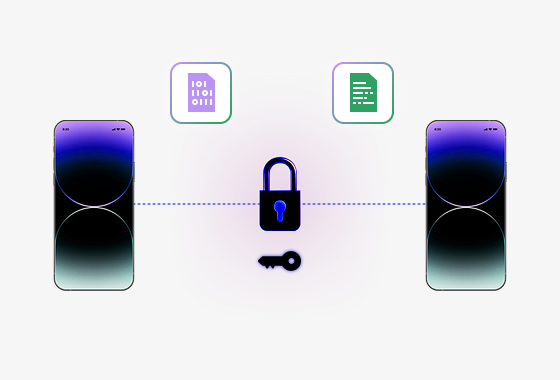
End-to-End Encryption
Secures communication and file exchange using full encryption protocols to protect confidential data across internal and external networks.
Features
Products
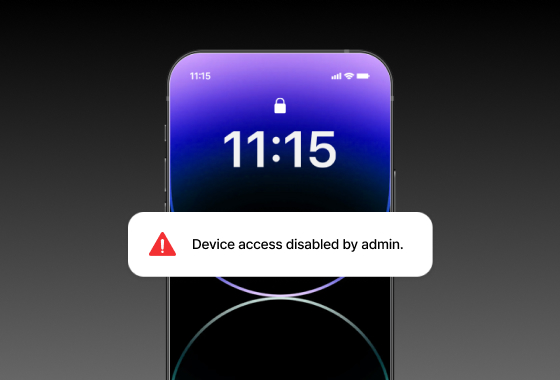
Remote Lock & Wipe
Remotely locks or wipes lost or stolen devices to ensure no classified or sensitive data can be retrieved.
Products
Reference Clients







